您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
網絡拓撲: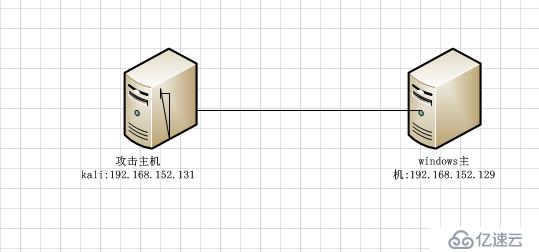
1.啟動postgresql數據庫:root@debian:~# service postgresql start
2.進入metasploit:root@debian:~# msfconsole
msf >
3.進行數據庫連接:
ms```
f > db_connect msf_user:111111@127.0.0.1/msf_database
[] Rebuilding the module cache in the background...
msf > db_status
[] postgresql connected to msf_database
4.利用nmap進行端口掃描
msf > db_nmap -sS 192.168.152.129
[] Nmap: Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-26 02:01 UTC
[] Nmap: Nmap scan report for 192.168.152.129
[] Nmap: Host is up (0.00043s latency).
[] Nmap: Not shown: 979 closed ports
[] Nmap: PORT STATE SERVICE
[] Nmap: 7/tcp open echo
[] Nmap: 9/tcp open discard
[] Nmap: 13/tcp open daytime
[] Nmap: 17/tcp open qotd
[] Nmap: 19/tcp open chargen
[] Nmap: 23/tcp open telnet
[] Nmap: 25/tcp open smtp
[] Nmap: 42/tcp open nameserver
[] Nmap: 53/tcp open domain
[] Nmap: 80/tcp open http
[] Nmap: 110/tcp open pop3
[] Nmap: 135/tcp open msrpc
[] Nmap: 139/tcp open netbios-ssn
[] Nmap: 445/tcp open microsoft-ds
[] Nmap: 1025/tcp open NFS-or-IIS
[] Nmap: 1028/tcp open unknown
[] Nmap: 1031/tcp open iad2
[] Nmap: 1032/tcp open iad3
[] Nmap: 1033/tcp open netinfo
[] Nmap: 1035/tcp open multidropper
[] Nmap: 1036/tcp open nsstp
[] Nmap: MAC Address: 00:0C:29:A2:5A:A9 (VMware)
[] Nmap: Nmap done: 1 IP address (1 host up) scanned in 8.59 seconds
已經將windows主機開放端口掃描出來免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。