您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
https://github.com/drwetter/testssl.sh
testssl.sh 是一個免費且開源的功能豐富的命令行工具,用于在 Linux/BSD 服務器上檢查支持加密,協議和一些加密缺陷的支持 TLS/SSL 加密的服務。
git clone --depth 1 --branch 2.9.5 https://github.com/drwetter/testssl.sh.gitFatal error: Neither "dig", "host", "drill" or "nslookup" is present
[root@localhost testssl.sh]# yum install bind-utils -y-b,-v:這2個是顯示版本的testssl自身的信息
-V:輸出現有的本機密碼套件列表
-t(--startssl):指明要測試的協議:
https ,ftp,smtp,pop3,imap,xmpp,telnet,ldap,postgres,mysql,
其中 telnet,ldap,postgres ,mysql 這4個協議要指定openssl
--mode < serial| parallel> 模式,默認是串行模式,若多核CPU大規模測試可選并行
--parallel:選項啟用并行測試 (默認是串行),等同于 --mode parallel
-e:測試每個密碼套件
-E:測試每個協議(SSL2 SSL3 TLS1 TLS1.1 TLS1.2
)
-s (--std):測試加密強度很高的一些密碼套件
-p(--protocols ) :測試每個TLS與SSL協議 并且檢測 spdy 與 http2
-S:測試并顯示服務器端證書信息
-P:測試并顯示服務器偏好(也就是服務器優先配置的TLS協議和密碼套件)
-x( --single-cipher <pattern> ): 指定一個密碼套件,也就是測試一下是否支持指定的這個套件
-c:測試客戶端支持情況
-h (--header):測試是否支持 HSTS, HPKP, cookie ,ipv4 ,代理 ,安全頭部等
-U:測試所有的漏洞
所有漏洞
-H, --heartbleed:tests for Heartbleed vulnerability
-I, --ccs, --ccs-injection:tests for CCS injection vulnerability
-T, --ticketbleed:tests for Ticketbleed vulnerability in BigIP loadbalancers
-R, --renegotiation:tests for renegotiation vulnerabilities
-C, --compression, --crime:tests for CRIME vulnerability (TLS compression issue)
-B, --breach:tests for BREACH vulnerability (HTTP compression issue)
-O, --poodle:tests for POODLE (SSL) vulnerability
-Z, --tls-fallback:checks TLS_FALLBACK_SCSV mitigation
-W, --sweet32:tests 64 bit block ciphers (3DES, RC2 and IDEA): SWEET32 vulnerability
-A, --beast:tests for BEAST vulnerability
-L, --lucky13:tests for LUCKY13
-F, --freak:tests for FREAK vulnerability
-J, --logjam:tests for LOGJAM vulnerability
-D, --drown:tests for DROWN vulnerability
-f, --pfs, --fs, --nsa:checks (perfect) forward secrecy settings
-4, --rc4, --appelbaum:which RC4 ciphers are being offered?
-6:支持ipv6
--ip [one]: 直接測試ip所指向的地址,不使用DNS解析出來的ip地址; 參數one 是指使用NDS解析返回的第一個IP地址,因為很多站點會有多個IP,那么會重復測試多次。
-n (--nodns) :不使用DNS
--sneaky:在服務器端少留痕跡
--quiet:不輸出banner
--fast:只顯示第一個密碼套件 與-P 合用
--log:輸出文檔(有默認名稱)
--logfile:指定一個輸出文檔
--json:json格式的文檔 (有默認名稱)
--jsonfile:指定一個json格式文檔
--csv:csv格式的文檔 (有默認名稱)
--csvfile:指定一個csv 格式文檔
--html:html 格式文檔 (有默認名)
--htmlfile:指定一個html文檔
--append:允許追加
[root@localhost testssl.sh]# ./testssl.sh --quiet 172.16.216.188
Start 2018-11-10 23:08:40 -->> 172.16.216.188:443 (172.16.216.188) <<--
rDNS (172.16.216.188): --
Service detected: HTTP
Testing protocols via sockets except SPDY+HTTP2
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered
TLS 1.1 offered
TLS 1.2 offered (OK)
SPDY/NPN http/1.1 (advertised)
HTTP2/ALPN http/1.1 (offered)
Testing ~standard cipher categories
NULL ciphers (no encryption) not offered (OK)
Anonymous NULL Ciphers (no authentication) not offered (OK)
Export ciphers (w/o ADH+NULL) not offered (OK)
LOW: 64 Bit + DES encryption (w/o export) not offered (OK)
Weak 128 Bit ciphers (SEED, IDEA, RC[2,4]) not offered (OK)
Triple DES Ciphers (Medium) not offered (OK)
High encryption (AES+Camellia, no AEAD) offered (OK)
Strong encryption (AEAD ciphers) offered (OK)
Testing robust (perfect) forward secrecy, (P)FS -- omitting Null Authentication/Encryption, 3DES, RC4
PFS is offered (OK) ECDHE-RSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-SHA
ECDHE-ECDSA-AES256-SHA ECDHE-RSA-AES128-GCM-SHA256 ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-SHA256 ECDHE-ECDSA-AES128-SHA
Elliptic curves offered: prime256v1 secp384r1 secp521r1 X25519 X448
Testing server preferences
Has server cipher order? yes (OK)
Negotiated protocol TLSv1.2
Negotiated cipher ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Cipher order
TLSv1: ECDHE-ECDSA-AES128-SHA ECDHE-ECDSA-AES256-SHA ECDHE-RSA-AES256-SHA AES128-SHA AES256-SHA
TLSv1.1: ECDHE-ECDSA-AES128-SHA ECDHE-ECDSA-AES256-SHA ECDHE-RSA-AES256-SHA AES128-SHA AES256-SHA
TLSv1.2: ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-GCM-SHA256
ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-SHA256 ECDHE-ECDSA-AES128-SHA ECDHE-ECDSA-AES256-SHA
ECDHE-RSA-AES256-SHA AES128-SHA AES256-SHA
Testing server defaults (Server Hello)
TLS extensions (standard) "renegotiation info/#65281" "EC point formats/#11" "session ticket/#35" "next protocol/#13172"
"max fragment length/#1" "application layer protocol negotiation/#16" "encrypt-then-mac/#22"
"extended master secret/#23"
Session Ticket RFC 5077 hint 300 seconds, session tickets keys seems to be rotated < daily
SSL Session ID support yes
Session Resumption Tickets: yes, ID: no
TLS clock skew Random values, no fingerprinting possible
Server Certificate #1 (in response to request w/o SNI)
Signature Algorithm ECDSA with SHA384
Server key size RSA 2048 bits
Fingerprint / Serial SHA1 126CAC24E8D08ED4BB90B330D166929C57D39A0D / 92F43BDFF9AC3B5CAA3189D661C69AFA
SHA256 5C9AD396AE017DC395BF9720D3D00BAC6C5C28CBF1AA2D921F32930B125F9336
Common Name (CN) www.linuxplus.com
subjectAltName (SAN) missing (NOT ok) -- Browsers are complaining
Issuer root_ca (CAdevops from CN)
Trust (hostname) certificate does not match supplied URI
Chain of trust NOT ok (chain incomplete)
EV cert (experimental) no
Certificate Expiration 294 >= 60 days (UTC: 2018-11-05 21:27 --> 2019-09-01 21:27)
# of certificates provided 1
Certificate Revocation List NOT ok -- neither CRL nor OCSP URI provided
OCSP URI --
OCSP stapling --
OCSP must staple no
DNS CAA RR (experimental) --
Certificate Transparency no
Server Certificate #2 (in response to request w/o SNI)
Signature Algorithm ECDSA with SHA256
Server key size ECDSA 256 bits
Fingerprint / Serial SHA1 F8DBD1BC27D744AC23C31C505C58FB55B33C7085 / 92F43BDFF9AC3B5CAA3189D661C69AFC
SHA256 5C7FAD30072D151AD5D6EA1EC0CCA669C6C7A1E8CB66E3AC2341502763723409
Common Name (CN) www.linuxplus.com
subjectAltName (SAN) missing (NOT ok) -- Browsers are complaining
Issuer root_ca (CAdevops from CN)
Trust (hostname) certificate does not match supplied URI
Chain of trust NOT ok (chain incomplete)
EV cert (experimental) no
Certificate Expiration 364 >= 60 days (UTC: 2018-11-10 22:32 --> 2019-11-10 22:32)
# of certificates provided 1
Certificate Revocation List NOT ok -- neither CRL nor OCSP URI provided
OCSP URI --
OCSP stapling --
OCSP must staple no
DNS CAA RR (experimental) --
Certificate Transparency no
Testing HTTP header response @ "/"
HTTP Status Code 200 OK
HTTP clock skew 0 sec from localtime
Strict Transport Security --
Public Key Pinning --
Server banner nginx/1.15.5
Application banner --
Cookie(s) (none issued at "/")
Security headers --
Reverse Proxy banner --
Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK), no heartbeat extension
CCS (CVE-2014-0224) not vulnerable (OK)
Ticketbleed (CVE-2016-9244), experiment. not vulnerable (OK)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation not vulnerable (OK)
CRIME, TLS (CVE-2012-4929) not vulnerable (OK)
BREACH (CVE-2013-3587) no HTTP compression (OK) - only supplied "/" tested
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507) Downgrade attack prevention supported (OK)
SWEET32 (CVE-2016-2183, CVE-2016-6329) not vulnerable (OK)
FREAK (CVE-2015-0204) not vulnerable (OK)
DROWN (CVE-2016-0800, CVE-2016-0703) not vulnerable on this host and port (OK)
make sure you don't use this certificate elsewhere with SSLv2 enabled services
https://censys.io/ipv4?q=5C9AD396AE017DC395BF9720D3D00BAC6C5C28CBF1AA2D921F32930B125F9336 could help you to find out
LOGJAM (CVE-2015-4000), experimental not vulnerable (OK): no DH EXPORT ciphers, no DH key detected
BEAST (CVE-2011-3389) TLS1: ECDHE-ECDSA-AES128-SHA ECDHE-ECDSA-AES256-SHA ECDHE-RSA-AES256-SHA AES128-SHA
AES256-SHA
VULNERABLE -- but also supports higher protocols (possible mitigation): TLSv1.1 TLSv1.2
LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)
Testing 359 ciphers via OpenSSL plus sockets against the server, ordered by encryption strength
Hexcode Cipher Suite Name (OpenSSL) KeyExch. Encryption Bits Cipher Suite Name (RFC)
-----------------------------------------------------------------------------------------------------------------------------
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc02c ECDHE-ECDSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
xc00a ECDHE-ECDSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc02b ECDHE-ECDSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc009 ECDHE-ECDSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
Running client simulations via sockets
Android 2.3.7 TLSv1.0 AES128-SHA
Android 4.1.1 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
Android 4.3 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
Android 4.4.2 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 5.0.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 6.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 7.0 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 253 bit ECDH (X25519)
Chrome 51 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 253 bit ECDH (X25519)
Chrome 57 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 253 bit ECDH (X25519)
Firefox 49 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Firefox 53 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 253 bit ECDH (X25519)
IE 6 XP No connection
IE 7 Vista TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
IE 8 XP No connection
IE 8 Win 7 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
IE 11 Win 7 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win 8.1 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win Phone 8.1 Update TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 11 Win 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win Phone 10 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Opera 17 Win 7 TLSv1.2 ECDHE-RSA-AES128-SHA256, 256 bit ECDH (P-256)
Safari 5.1.9 OS X 10.6.8 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
Safari 7 iOS 7.1 TLSv1.2 ECDHE-RSA-AES128-SHA256, 256 bit ECDH (P-256)
Safari 9 OS X 10.11 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Safari 10 OS X 10.12 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Apple ATS 9 iOS 9 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Tor 17.0.9 Win 7 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
Java 6u45 TLSv1.0 AES128-SHA
Java 7u25 TLSv1.0 ECDHE-ECDSA-AES128-SHA, 256 bit ECDH (P-256)
Java 8u31 TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
OpenSSL 1.0.1l TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
OpenSSL 1.0.2e TLSv1.2 ECDHE-ECDSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Done 2018-11-10 23:10:25 [ 107s] -->> 172.16.216.188:443 (172.16.216.188) <<--
[root@www testssl.sh]# ./testssl.sh -c --quiet --html 172.16.216.188
[root@www testssl.sh]# ll *.html
-rw-r--r--. 1 root root 5687 11月 24 15:59 172.16.216.188_p443-20181124-1558.html
[root@www testssl.sh]# ./testssl.sh -c --quiet --log 172.16.216.188
[root@www testssl.sh]# ll *.log
-rw-r--r--. 1 root root 985 11月 24 16:04 172.16.216.188_p443-20181124-1604.log[root@www testssl.sh]# ./testssl.sh --quiet -U 172.16.216.188
Start 2018-11-24 16:06:40 -->> 172.16.216.188:443 (172.16.216.188) <<--
rDNS (172.16.216.188): --
Service detected: HTTP
Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK), no heartbeat extension
CCS (CVE-2014-0224) not vulnerable (OK)
Ticketbleed (CVE-2016-9244), experiment. not vulnerable (OK)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation not vulnerable (OK)
CRIME, TLS (CVE-2012-4929) not vulnerable (OK)
BREACH (CVE-2013-3587) no HTTP compression (OK) - only supplied "/" tested
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507) Downgrade attack prevention supported (OK)
SWEET32 (CVE-2016-2183, CVE-2016-6329) not vulnerable (OK)
FREAK (CVE-2015-0204) not vulnerable (OK)
DROWN (CVE-2016-0800, CVE-2016-0703) not vulnerable on this host and port (OK)
make sure you don't use this certificate elsewhere with SSLv2 enabled services
https://censys.io/ipv4?q=5C9AD396AE017DC395BF9720D3D00BAC6C5C28CBF1AA2D921F32930B125F9336 could help you to find out
LOGJAM (CVE-2015-4000), experimental not vulnerable (OK): no DH EXPORT ciphers, no DH key detected
BEAST (CVE-2011-3389) TLS1: ECDHE-ECDSA-AES128-SHA ECDHE-ECDSA-AES256-SHA ECDHE-RSA-AES256-SHA AES128-SHA
AES256-SHA
VULNERABLE -- but also supports higher protocols (possible mitigation): TLSv1.1 TLSv1.2
LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)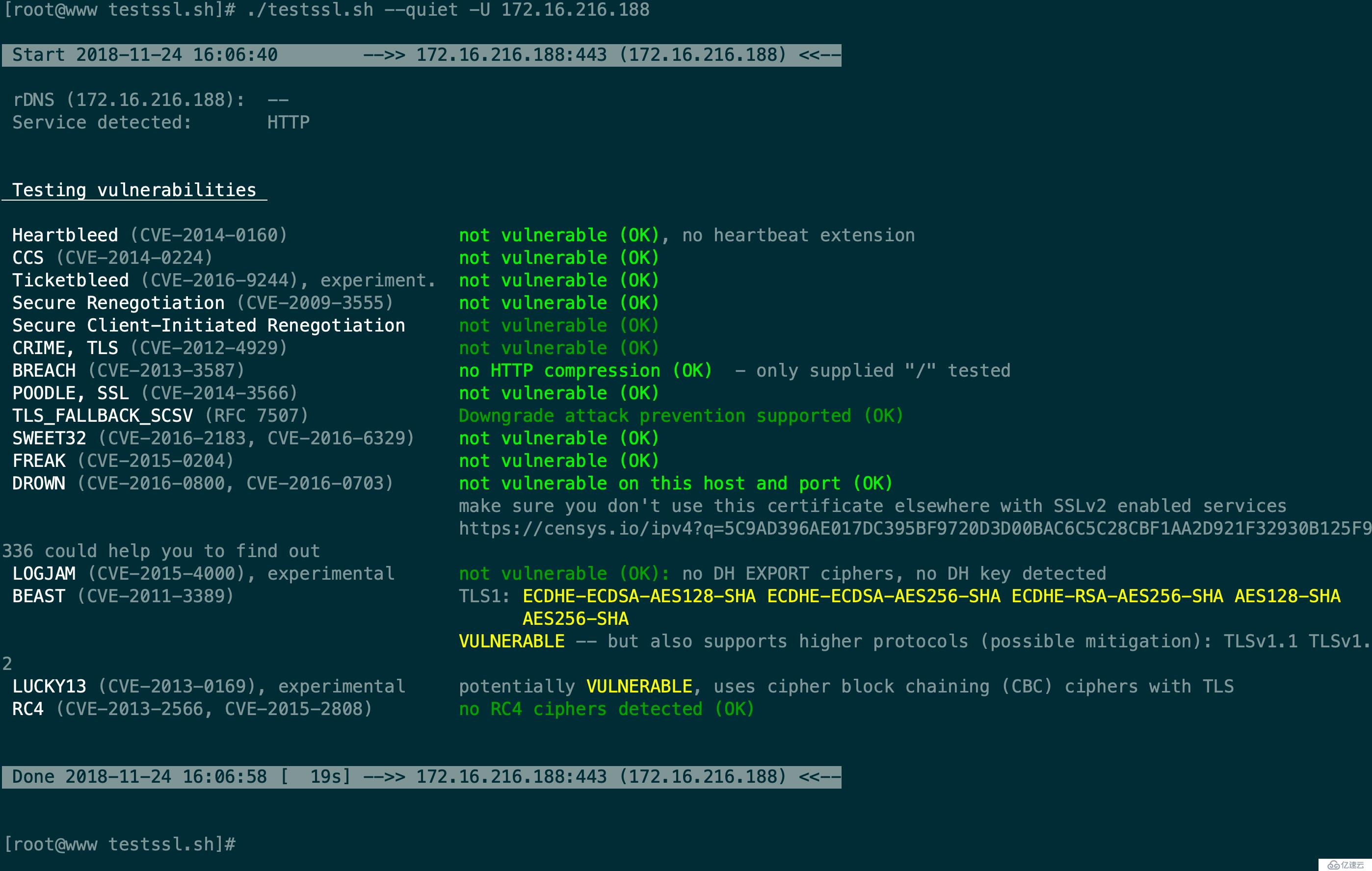
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。